Information incidents are increasing in scale, scope and complexity. From coordinated harassment campaigns (e.g. spamouflage, October 2023) to information interference (e.g. Meta’s news block in Canada, August 2023), the need is increasing to be able to find ways to identify, characterize, manage and learn from information incidents and how to build a more resilient information ecosystem.
What is an information incident?
A disruption in the information ecosystem, including both sudden and prolonged interruptions, that significantly impacts the normal flow and/or integrity of information, leading to potential or actual harm to the public, government, Canadian democracy, and/or the broader information ecosystem.
What are we hoping to achieve?
In response to this need, the Project on Information Ecosystem Resilience (PIER) is an innovative research project that has emerged to support civil society organizations, government, media, public and private institutions to prevent and mitigate, prepare for, respond to and recover from information incidents, and improve information ecosystem resilience.
This PIER project aims to achieve its goal through three main objectives:
MONITOR : Provide baseline understanding of the information ecosystem conceptualizing information flows, influence, sources and effects of mis/disinformation and interference, and anomalies as it relates to media, public perception and the political discourse
NOTIFY : Monitor and identify information incidents as they occur, provide ongoing updates as an incident evolves, and characterize ripple effects to inform future planning and lessons learned, and
EVOLVE : Improve information ecosystem resilience through initiatives like (mis)information literacy public education programming or policy guidance materials.
How do we do it?
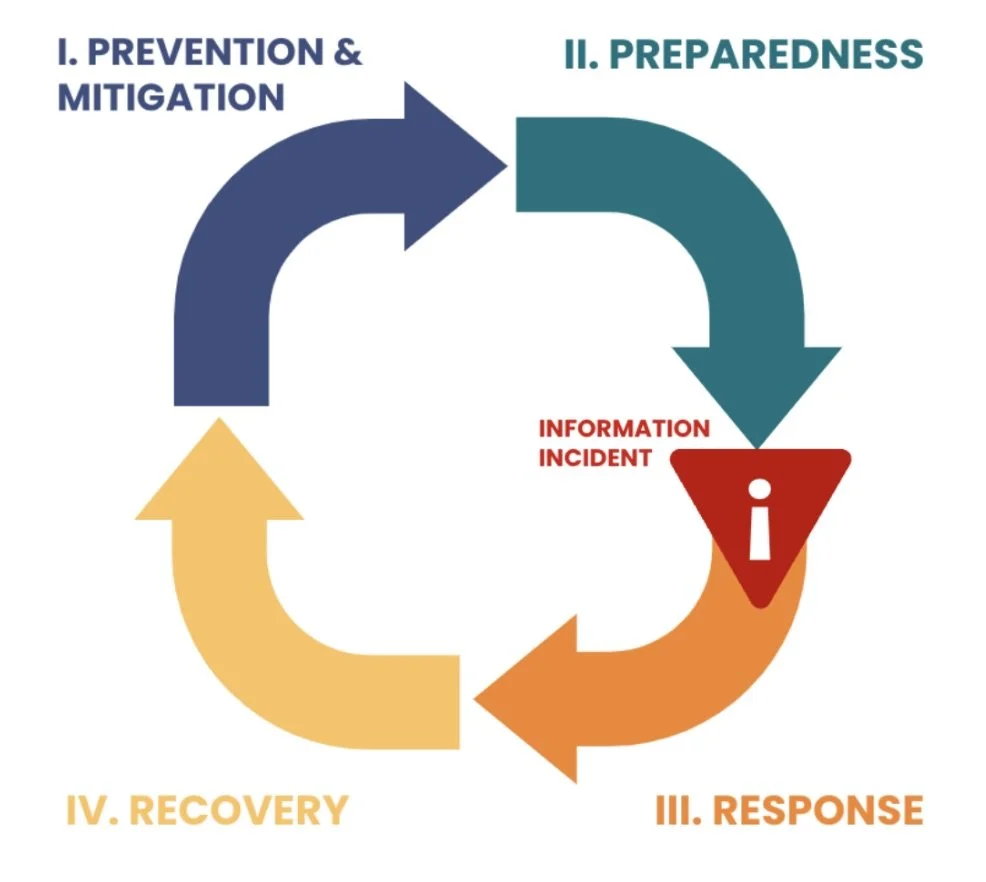
To achieve its objectives, PIER uses the disaster and emergency management cycle as a foundation to ensure activities focus on building resilience in the face of information incidents. This cycle consists of four interdependent phases that can occur sequentially or concurrently across all stages of an incident. Broadly, they fall within a period of normal operations (information ecosystem is in a stable state, information flows continue as normal with minimal fluctuation) and incident operations (information ecosystem is destabilized, information has emerged that has a minor to significant ripple effect on system dynamics).
Prevention & Mitigation: Actions taken to adapt to, identify, prevent, eliminate or reduce the risk and impact of incidents (e.g. digital literacy, platform governance, building transparency).
Preparedness: Actions taken prior to an incident to prepare for response and recovery (e.g. characterizing, monitoring & analyzing ecosystem health, vulnerability and information threats).
Response: Actions taken in direct response to an imminent or ongoing incident to manage consequences (e.g. alerting the public of information incidents, providing updates, and correcting falsehoods).
Recovery: Actions taken to repair and/or restore conditions to a tolerable or improved level (e.g. characterizing and analyzing the impact of information incidents).
Note: Phases are undertaken concurrently or sequentially, with core activities and outputs associated with each phase.
What are we doing?
To achieve our objectives PIER has two main operation modes:
Baseline operations: Ongoing monitoring, alerting and ecosystem evolution efforts.
Event-specific operations: Targeted and customized monitoring, alerting and ecosystem evolution efforts specific to upcoming or immediate events that disrupt the ecosystem, e.g. elections, political gatherings like the G7, health emergencies like pandemics, and natural events like wildfires.
What do we deliver?
In order to be as efficient as possible, our PIER activities span the emergency management cycle and include ongoing activities and event-specific operations.
Ongoing Activities
Situation reports: Monthly public-facing reports measuring overall information ecosystem health, identifying system vulnerabilities (toxicity, trust, polarity, inequality) and current and emerging information threats (including cases of misinformation, disinformation and interference).
Information incident notifications and updates: When an information incident is identified, notifications are issued within 24 hours and subsequent updates are provided to follow the incident. Notifications describe and track the incident, provide any necessary background context, describe potential impacts, areas for further investigation and key contacts.
Information incident analysis reports: For major incidents, PIER conducts detailed research and publishes a full public-facing debrief paper focused on evaluating nature and impact of the incident on the information ecosystem, and valuable lessons learned.
Event-Specific Operations
Pre-event information ecosystem reports: An analysis of the state of the information ecosystem up to one year leading up to the event (depending on the scale of the event). Reports highlight event-relevant information ecosystem characteristics and trend patterns, as well as current and emerging vulnerabilities and threats (include the current interference landscape).
Post-election analysis report: A full-scale evaluation of all information events that have occurred during the event period. Analysis will explore social discussion of the incident (e.g. awareness and perceptions), conduct causal evaluation of shifts in population-level attitudes, and identify lessons learned.